User attributes
When using single sign-on with SAML or JWT, you can define some attributes of users in Veezoo based on values from the authentication token:
- when using SAML: based on attributes from the SAML assertion
- when using JWT: based on claims from the JWT
Attributes
The following attributes can be configured:
| Attribute | Description | Multi-valued |
|---|---|---|
| Tenant | The tenant the user belongs to (only available when using multi-tenancy) | no |
| Type | The user's type, i.e. if the user is a Creator or a Viewer | no |
| First name | The user's first name | no |
| Last name | The user's last name | no |
| The user's e-mail address | no | |
| Language | The user's preferred language, if supported by a given knowledge graph | no |
| Roles | The user's roles | yes |
Mapping
For each user attribute, you can define one or more mappings that determine the value of the attribute. When a user authenticates, i.e. opens or reloads Veezoo in their browser, the mappings are evaluated and the corresponding user attributes are updated accordingly.
Mappings are evaluated in order from top to bottom:
- for single-valued user attributes, the first matching mapping us used
- for multi-valued user attributes, all matching mappings are applied.
Each mapping consists of the following fields:
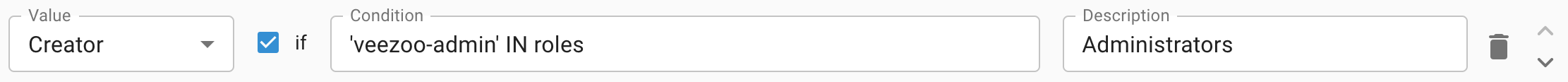
Value
The value to assign to the user attribute, if the condition holds.
For some user attributes (e.g. type), the permitted values are predefined and can be selected using a dropdown. For other attributes (e.g. first name), the entered value must be a variable or a string.
Condition
The condition which determines if the mapping should be used (optional).
If set, then the mapping's value is only assigned to the user attribute if the condition holds, else the mapping is ignored. The entered value must be a condition.
Description
The description for the mapping (optional).
Syntax
The following simple syntax can be used to express conditions and reference attributes from the authentication token (i.e. SAML assertion attributes or JWT claims).
String
A string is enclosed in single quotes.
Example: 'abc'
Array
An array encloses a comma-separated list of strings in brackets.
Example: ['a', 'b', 'c']
Variable
A variable references an attribute from the authentication token, i.e. a SAML assertion attribute or JWT claim).
If the variable contains non-alphanumerical characters, then it needs to be enclosed in backticks.
Examples:
firstName`first-name``http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname`
Condition
A condition consists of a left-hand side, an operator and a right-hand side.
| Operator | Name | Description |
|---|---|---|
== | Equality | Evaluates to true if the left-hand side is equal to the right-hand side |
!= | Non-equality | Evaluates to true if the left-hand side is not equal to the right-hand side |
IN | Containment | Evaluates to true if the left-hand side is contained in the right-hand side |
NOT IN | Non-containment | Evaluates to true if the left-hand side is not contained in the right-hand side |
AND / && | Conjunction | Evaluates to true if both the left-hand side and right-hand side evaluate to true |
OR / | | Disjunction | Evaluates to true if either of the left-hand side and right-hand side evaluate to true |
NO / ! | Negation | Negates the result of the condition |
Examples:
- Equality:
language == 'fr'departmentCodes == ['D1', 'D2'] - Non-equality:
language != 'fr'departmentCodes != ['D1', 'D2'] - Containment:
departmentCode IN ['D1', 'D2', 'D3']'D1' IN departmentCodes - Non-containment:
departmentCode NOT IN ['D1', 'D2', 'D3']'D1' NOT IN departmentCodes - Conjunction:
language == 'fr' && departmentCode IN ['D1', 'D2', 'D3'] - Disjunction:
language == 'fr' || departmentCode IN ['D1', 'D2', 'D3'] - Negation:
NOT language == 'fr'! language == 'fr' - Parentheses:
!(language == 'fr')((a == '1' OR a == '2') AND NOT(b == '3'))
- A string is considered to be equal to an array holding exactly that string
E.g.
'a' == ['a']holds true - The left-hand side of a (non-)containment condition can be an array
E.g.
['b', 'a'] IN ['a', 'b', 'c']holds true
Examples
Consider the following SAML assertion:
<samlp:Response ...>
...
<saml:AttributeStatement>
<saml:Attribute Name="firstName" ...>
<saml:AttributeValue ...>John</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="departmentCode" ...>
<saml:AttributeValue ...>D1</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="language" ...>
<saml:AttributeValue ...>fr</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="roles" ...>
<saml:AttributeValue ...>internal-admin</saml:AttributeValue>
<saml:AttributeValue ...>veezoo-admin</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
...
</samlp:Response>
The following examples illustrate some mappings and what they evaluate to given the above SAML assertion:

→ The mapping matches and evaluates to abc

→ The mapping matches and evaluates to John

→ The mapping matches and evaluates to John
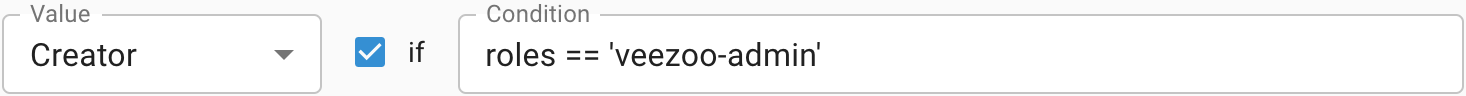
→ The mapping doesn't match
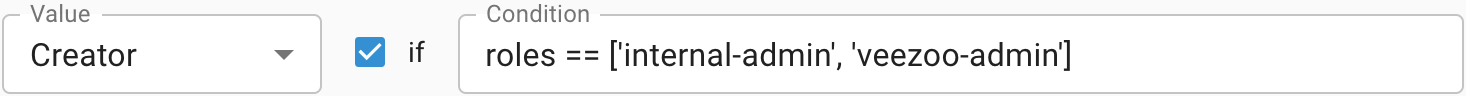
→ The mapping matches and evaluates to Creator
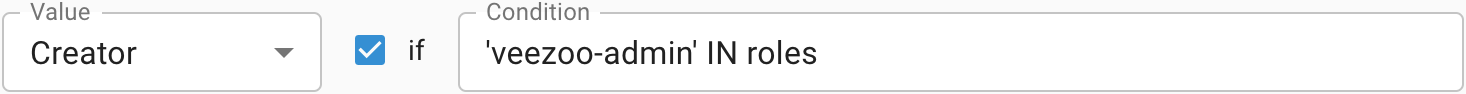
→ The mapping matches and evaluates to Creator
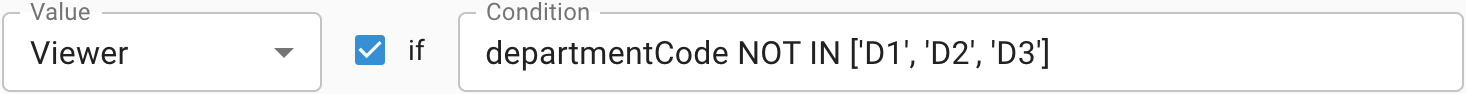
→ The mapping doesn't match

→ The mapping matches and evaluates to Français

→ The mapping matches and evaluates to the empty string